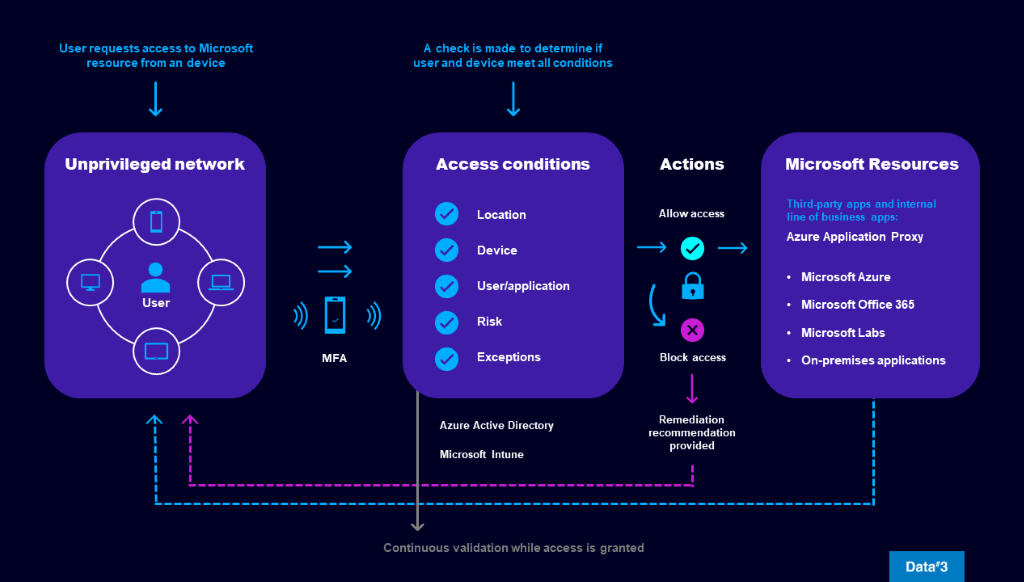
Advanced Threat Protection (ATP)
ATP helps secure you the most fundamental and primary communication methods such as email, web, and collaboration tools. Malicious content in emails and websites is, and remains, one of the most pervasive problems in cybersecurity.
Business email compromise is a major challenge for Australian businesses, with around 20% of all business email attacks globally targeting Australian companies1.
Forrester found that ATP – built-in to Windows 10 – contributed to a 40% reduction in risk of a data breach and caught 1.7 times as many threats as other endpoint detection and response tools2.