Contact us
For more information please contact one of our Solution or Service experts today.
Information provided within this form will be handled in accordance with our privacy statement.

See the real-world benefits of moving to Cisco Secure Access—stronger protection, simpler policy…
Three overlooked apps every organisation should use When you think of Adobe Creative Cloud, the…

Upgrade from Cisco Umbrella to Secure Access the smart way—protect users, reduce risk, and migrate…

When it comes to cyber security, external attacks often dominate the headlines, but some of the most…

February 4, 2026; Brisbane, Australia: Leading Australian technology services and solutions provider,…

Australian Catholic University shapes the future of learning with Microsoft Azure.

Containerised and hybrid workloads can become black boxes. Learn how Cisco Smart Switches restore…

Examine what it takes to prepare your switching environment for AI.

In today’s hyperconnected world, data security can feel like a puzzle that’s constantly changing….
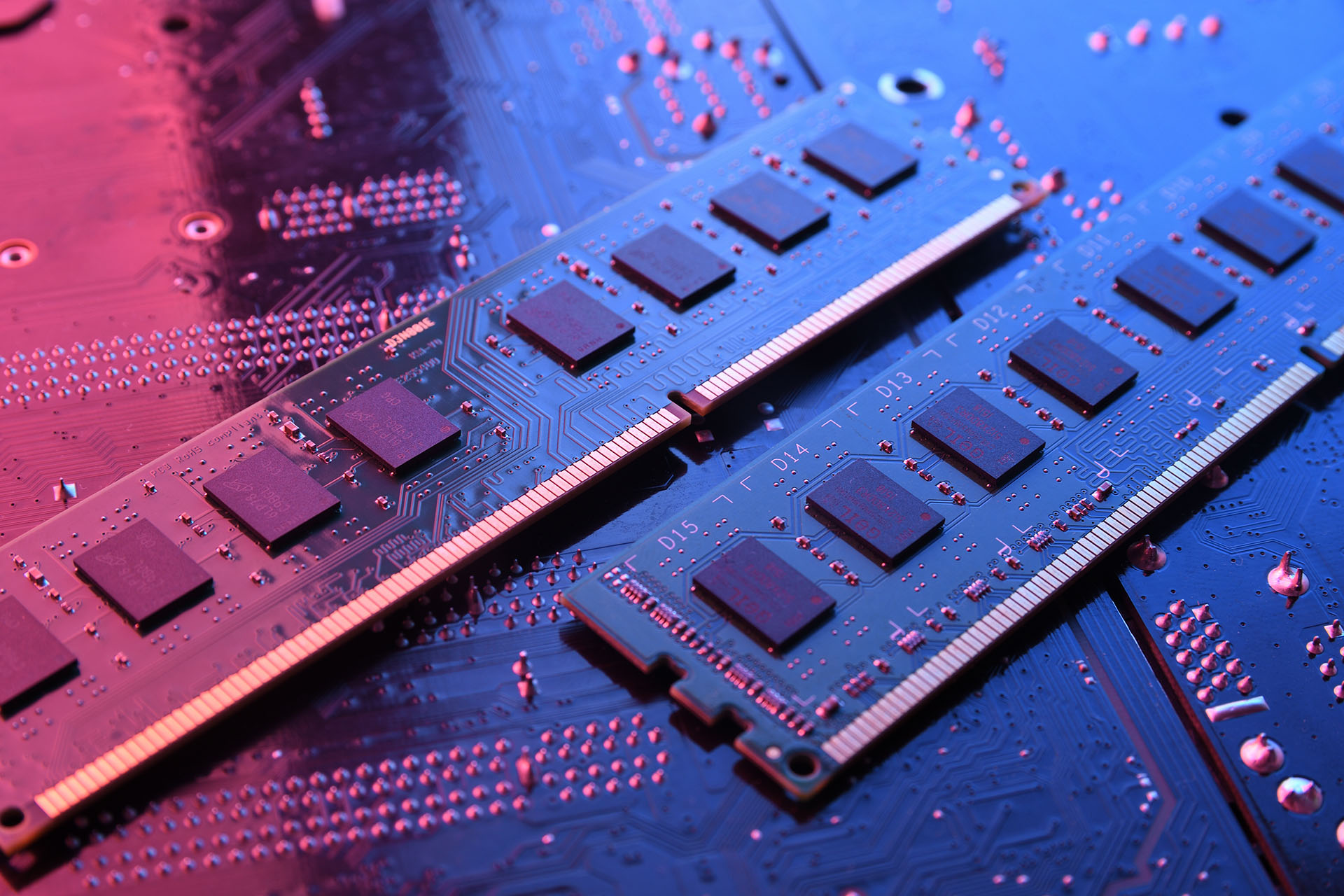
In September 2025, a 32GB DDR5 memory module cost about US$95. By December, that same module was selling…

Data#3 General Manager for NSW, Paul Crouch, has announced his retirement after more than two decades of…

As networks become more distributed, security must move closer to the workload. Discover how Cisco Smart…

For more information please contact one of our Solution or Service experts today.

For more information please contact one of our Solution or Service experts today.
Information provided within this form will be handled in accordance with our privacy statement.