Cyberattacks to businesses via IT Supply Chains are increasing at 42% Quarter on Quarter (QOQ) Q420-Q121.
Lenovo’s industry-recognised supply chain gives you the peace of mind you didn’t realise you needed, by using a multi-layered approach to secure your IT supply chain before you have even ordered your infrastructure.
Lenovo’s supply chain is the secure foundation for your IT infrastructure:
By compromising a single supplier, external agents can hijack its distribution systems to turn any application they sell, any software update they push out, even the physical equipment they ship to customers, into Trojan horses. With one well-placed intrusion, they can create a springboard into your network.
The most recent high-profile example of this is the SolarWinds attack in 2020, where Russian hackers used its software to distribute trojanised updates to the software’s users.
The Australian Cyber Security Centre has released a document regarding Cyber Supply Chain Risk Management, where it emphasises how (with Australia’s Privacy laws) an organisation will transfer any cyber supply chain risk they hold to their customers. This essentially means that you take ownership for your supply chain as far as the law is concerned.
While the software supply chain is the “easier” attack vector in the supply chain, physical attacks are also increasing.
The complexity of technology supply chains introduces many opportunities for risk. A compromise at any of the points between component suppliers, Original Equipment Manufacturers (OEM) and customers in the supply chain can put the integrity of the device at risk. Vulnerabilities in any components could allow malicious actors to tamper with the device later in the supply chain.
Lenovo offers an unparalleled level of transparency and security to its customers by pairing its industry leading supply chain with the Intel Transparent Supply Chain program. This approach adds a layer of protection to your data centre and provides peace of mind that the server hardware you bring into it is safe, authentic and with documented, testable, and provable origin.
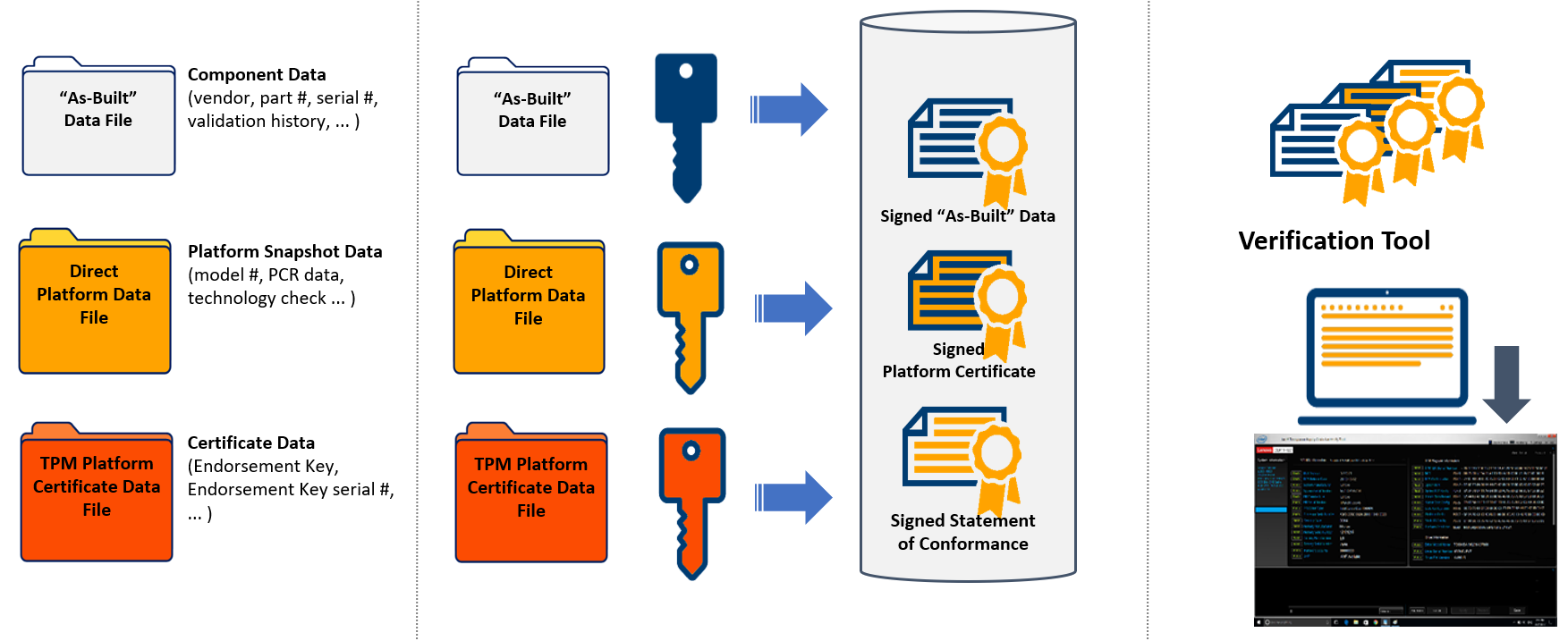
Figure 2 – Typical Physical Supply Chain illustrating areas of potential risk1
Many of the measures employed by Lenovo cover the points raised by the Australian Cyber Security Centre on identifying cyber supply chain risks.
Lenovo also employs a multi-layered approach to provide a foundation of security built-in to its products
To assure customers can depend on every part of Lenovo’s supply chain, Lenovo created the Trusted Supplier Program. The program’s goal is simple: to ensure that every supplier meets high security standards set by Lenovo’s customers.
So how does Lenovo’s Trusted Supplier Program work? The program provides customers security assurance by:
Lenovo also evaluates each supplier’s development and manufacturing process to help them identify and mitigate security risks. Suppliers are subject to re-evaluation on a regular basis, requiring an ongoing effort to keep up to date with industry best practices and processes around security.
The program covers “intelligent components,” which are broadly defined as any:
Lenovo own and operate their own factories in multiple locations around the globe. This helps Lenovo maintain continuous oversight & security of their operations, and maintains that critical link in the supply chain.
Having thirty facilities in various locations around the globe also allows Lenovo quickly react to changing conditions. This was used successfully during the COVID-19 pandemic when factories in one part of the world needed to close during local outbreaks, but the slack was picked up by factories in another region.
The first step to having secure firmware is to develop, store and sign it in a secure location. To maintain compliance with US Government audits, Lenovo stores and signs its source code in its US-based operational headquarters.
With their security processes for development reviewed and approved by the US Government, this ensures peace of mind for organisations concerned with Lenovo having a headquarters in China, also.
To protect against tampered firmware, Lenovo utilise the TPM (Trusted Platform Module) together with Secure Boot to ensure the integrity of the platform. It is to ensure that the boot process starts from a trusted combination of hardware and software, and continues until the operating system has fully booted and applications are running.
The ACSC has provided Australian businesses and consumers guidelines to follow to help manage their cyber supply chain and identify cyber supply chain risks. Lenovo’s industry-recognised supply chain has already taken the time to tick most of these boxes for you, and to ensure that the next server you purchase comes precisely as ordered. Contact a Data#3 Lenovo specialist to discuss how we can help you leverage Lenovo technology in your organisation.
1. Lenovo Press (2021) Introduction to Intel Transparent Supply Chain on Lenovo ThinkSystem Servers [Online] https://lenovopress.com/lp1434-introduction-to-intel-transparent-supply-chain-on-lenovo-thinksystem-servershttps://www.researchgate.net/publication/6795797_How_far_do_nurses_walk