
A weakness has been discovered in Microsoft Teams that allows attackers to deliver malicious files to users if Microsoft Teams is configured to allow external parties to establish chat.
There is a simple fix for the exploit called TeamsPhisher. Businesses should disable external access and allow only trusted domains to initiate chats from external parties, as by default, when Microsoft Teams is configured to enable external access, it allows access to anyone.
Max Corbridge and Tom Ellson of JUMPSEC’s Red Team have discovered a vulnerability in the most recent version of Microsoft Teams which was published on June 21, 2023.
The exploit takes advantage of the default setting of Microsoft Teams, which permits users from outside tenants to chat with employees in businesses.
Threat actors can transmit payloads right into a target’s Microsoft Teams chat by faking recipient IDs in POST requests.
These payloads appear as files in the target’s Microsoft Teams environment and are hosted on SharePoint sites. The flaw gets around standard anti-phishing security measures, instigating a channel for threat actors to distribute malicious files.
Upon notifying Microsoft of the vulnerability, JUMPSEC received confirmation that it is a legitimate vulnerability. However, Microsoft found that it did not satisfy the requirements for immediate service, indicating that a fix, or patch for the issue may not become immediately available.
The following steps should be taken by organisations to reduce the risks posed by this vulnerability:
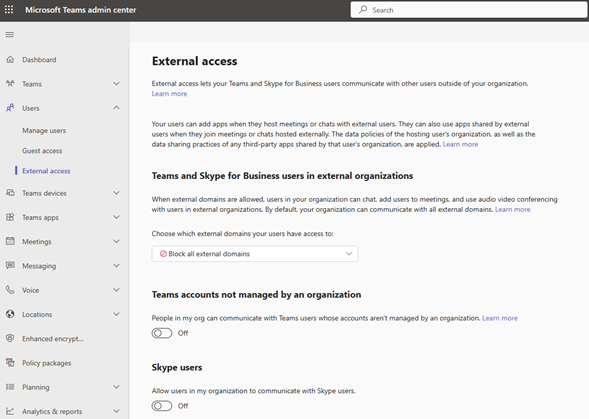
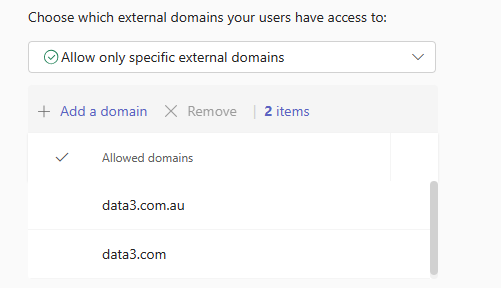
Or;
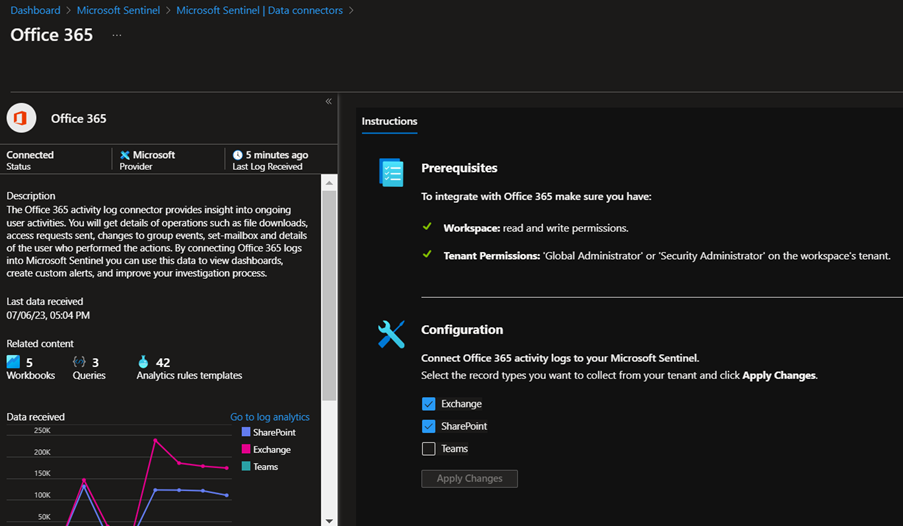
Azure Sentinel is your go-to resource for reporting on external collaboration activity. If you have deployed Azure Sentinel and configured the Microsoft 365 connector, then it is a simple operation to enable Microsoft Teams ingestion on the connector page. This is a new feature so if you have enabled the connector previously then the Microsoft Teams option might not have been available at the time.
If you are not familiar with what external domains may be communicating with your Microsoft Teams instance, Data#3 can help you identifying external domains and validate trusted from unknown sources. If your Microsoft 365 tenant doesn’t have strict controls in place to ensure it is well-governed, start with a Microsoft 365 Health check today.
If you need ongoing support managing Microsoft 365 licensing and governance, we recommend the Microsoft 365 Optimiser service. As an Azure Expert MSP, if you’re interested in deploying Azure Sentinel, we can help with that too.
Information provided within this form will be handled in accordance with our privacy statement.